I’ve had many roles in my network engineering career that have led to my current position as Chief Technology and Development Officer at Betacom. I have to say that network security has been a critical issue throughout my career, but I cannot remember a time when it has been more crucial, with the potential for creating greater harm. We’ve all seen the increase in ransomware and hacking attacks in the news over the past few years – often targeting key infrastructure businesses. With the rise of cybersecurity threats occurring at the same time as enterprises are accelerating their digital transformation projects, security is of paramount importance.
Enterprises require secure data networks that can be trusted with business-critical tasks, especially for Industrial IoT applications, and they are increasingly interested in owning their own wireless networks to maintain control over their data and network performance. Security has become a key consideration as Enterprises start to evaluate private wireless networks as a high performance option for managing essential business applications and operations. What are the elements that make a private 4G/5G network secure? What are the advantages of a private network over a public network? What factors should be explored in evaluating the differences between private network solutions on the market?
Security is a process, not a product.
Bruce Schneier
Bruce Schneier is a security guru who has been working in the industry for over two decades. I agree with his view about the importance of process when designing and deploying security systems, and I want to take it one step further. At Betacom we have built the process of security into every element of our 5G-as-a-Service (5GaaS) solution.
Built on global 3GPP standards that have been hardened for years, the security advantages of 4G/5G networks are well-established. 4G networks use SIMs and multifactor authentication to help ensure authorized access to the network. 5G adds new protections at the device, radio and core network layers to authenticate and isolate devices, making it possible to securely deploy a wide range of machines, robots and sensors to enable Industry 4.0 use cases.
In building our 5GaaS solution, my team has added to this security foundation by addressing security at every stage of our managed service offering with a Zero Trust design principle. We manage the network from a modern Security and Service Operations Center (SSOC). The SSOC is enabled with cloud-based applications that use Artificial Intelligence and Machine Learning (AI/ML) to proactively monitor the network and respond to threats in real time. All network components are deployed behind the Enterprise firewall, and traffic is separated so that Enterprise data stays inside their business. The control plane data we use to monitor and manage the network is encrypted end-to-end, adding additional security without impacting network performance or bandwidth.
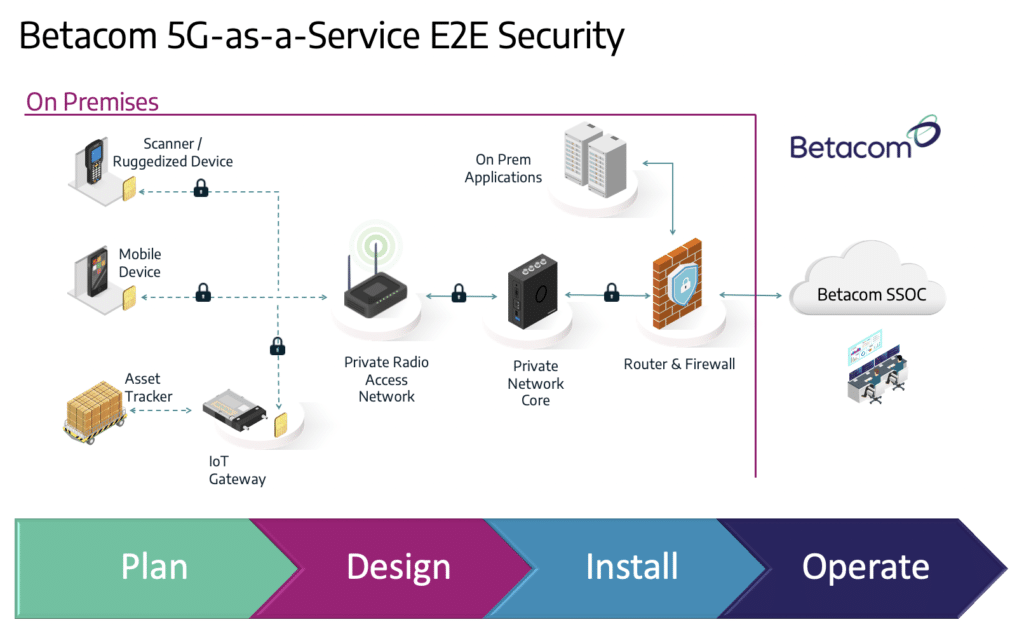
Here are some of the key security elements that we’ve designed into each phase of service delivery to ensure end-to-end solution security:
Plan
Security starts in planning stage. Along with establishing the detailed technical and performance requirements and establishing the applications that will run on the network, we work with our customers to establish the security and policy principles for the network. We meet with the IT team to understand how our private wireless infrastructure will interconnect with the existing LAN/WAN infrastructure and how to best deploy the private wireless network to reach back-end application systems and interconnect with our SSOC. This ensures that we understand the Enterprise business, security concerns, and network and security systems in place so that we can design appropriately and deliver against specific requirements.
Design
During the design phase we establish the network architecture. This includes laying out the nodes that will be accessing the network, and what devices will be accessing these nodes and from where. We take into account the existing security infrastructure and help make informed decisions about additional security measures that might be needed. The deliverables from this phase include the location of all required private wireless equipment (private radio access network, private wireless core and security gateways), an RF design that shows a heat map of coverage, a full bill of materials (BOM), and mutual decisions about where the network will reside.
Install
Before we step foot on a new installation site we stage the private network in order to harden the security of each element in 5GaaS. We then install the system behind the Enterprise firewall, ensuring that each network element is connected over a secure channel. Our highly trained installation crews have in-depth expertise in deploying 4G/5G networks, limiting risk associated with deployments. Our teams are focused on understanding precise requirements and troubleshooting needs with risk avoidance strategies to keep projects on track and within budget. In addition to performance tests, we will run security tests to ensure the network is running as designed.
Operate
Once we’ve installed the Betacom 5GaaS network, our managed service value begins as we proactively monitor the network 24×7 from our SSOC. We leverage AI/ML applications to detect system anomalies, alerts or alarms. Our SSOC then proactively assesses and guides response actions to ensure a continuously available service. The AIOps system continuously trains as new threat behavior is detected and new rules are created. Enterprises have dashboard access into network performance for additional assurance that the private wireless network is performing as specified. We run periodic vulnerability scans to ensure the setup continues to be protected and has the latest updates. My SSOC team of U.S. based engineers is also available 24×7 to proactively address issues.
Private wireless networks offer Enterprises a new connectivity option for business-critical applications that require reliable high-speed, low latency performance. Betacom 5GaaS is founded on 4G/5G standards and is managed through our Security and Service Operations Center with the latest in AIOps and cybersecurity management to give our customers the peace of mind that all elements of security have been designed into the solution with zero trust principles. Security is not an afterthought or a product feature. It is a design principle and a process that drives every aspect of our managed private network service.
Venkat Ramachandran
CTO
Betacom
